advertisement
Spammers Employ Agent Tesla Stealer In Targeted Email Campaigns

Cybersecurity company Kaspersky has uncovered an unsual spam email campaign that targetegd business worldwide.
Mimicking emails from vendors or counterparty companies, the attackers tried to steal the login data from the affected organisations by applying notorious Agent stealer. These credentials might be offered for sale on darkweb forums or used in targeted attacks against these organisations.
Today, cybercriminals are investing efforts into mass spam campaigns – and the recent investigation conducted by Kaspersky provides a clear proof of this. The uncovered spam email campaign, aimed at various organisations, contained high-quality imitations of business inquiries by real companies, only given away by the inappropriate sender addresses. Moreover, as a payload the attackers used the Agent Tesla stealer – a well-known Trojan Spy malware, designed to steal authentication data, screenshots, and data captured from web cameras and keyboards. The malware was distributed as a self-extracting archive attached to the weaponised email.
advertisement
In one email example, someone posing as a Malaysian prospect uses an odd variety of English to ask the recipient to review some customer requirements and get back with the requested documents. The general format complies with the corporate correspondence standards: there is a logo that belongs to a real company and a signature that features sender details. Overall, the request looks legitimate, while the linguistic errors can be easily attributed to the sender who is a non-native speaker.
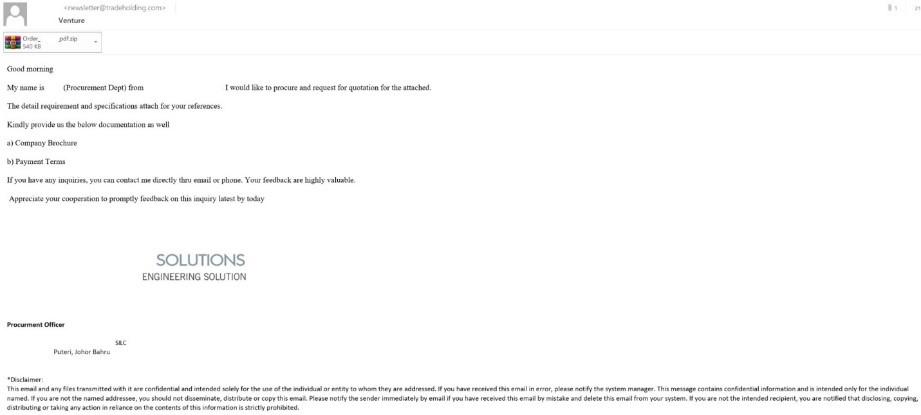
The only suspicious thing about the email is the sender’s address, newsletter@trade***.com, is labeled as a “newsletter”, typically used for news, not procurement. Besides, the sender’s domain name is different from the company name in the logo.
In another email, a purported Bulgarian customer makes an enquiry about the availability of some products and offers to discuss the details of a deal. The requested product list is said to be in the attachment, as in the previous specimen. The sender’s address, similarly suspicious, belongs to a Greek, not Bulgarian, domain, which apparently has no relation to the company whose name is used by the spammers.
advertisement
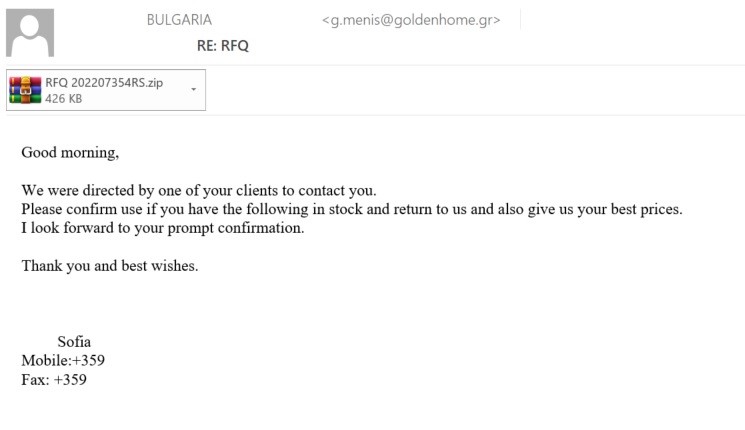
The messages originated within a limited range of IP addresses and the attached archives contained the same malware, Agent Tesla – that makes the researchers think that all these messages were part of one targeted campaign.
“Agent Tesla is a highly popular stealer used to fetch passwords and other credentials from affected organisations. It’s been known since 2014 and deployed by spammers widely in mass attacks. However, in this campaign cybercriminals took on techniques that are typical of targeted attacks – the sent emails were tailored especially for the company of interest and are barely different from legitimate ones,” adds Roman Dedenok, security expert at Kaspersky.
Kaspersky products detect Agent Tesla stealer as Trojan-PSW.MSIL.Agensla.