dx100 Awards: Connecting The Dots In Cyber Security
Security in digital transformation is a very crucial topic that is also becoming too wide to unpack in a short…

Security in digital transformation is a very crucial topic that is also becoming too wide to unpack in a short…

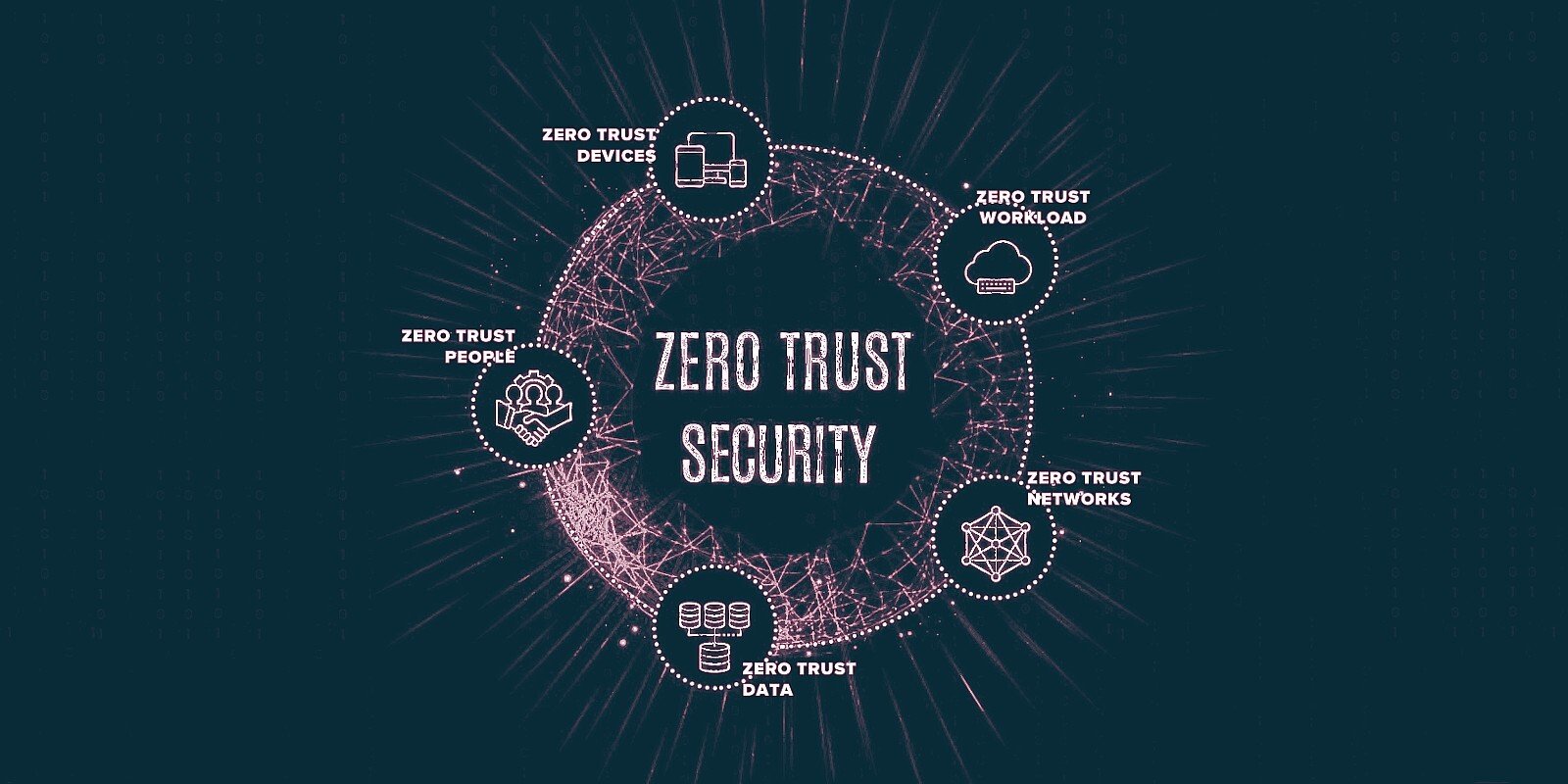
When talking about taking a Zero-Trust approach to the cybersecurity of your firm, it is important to note that Zero-Trust…

You have been hacked. What next? With an increase in cyber threats, organisations need not only to protect themselves against…

Sophistication and the severity of cybersecurity attacks have increased in the last two years as organisations embraced remote-working and shifted…

Conti Gang Encrypts Karma’s Extortion Notes in Dual Ransomware Attack, Sophos Research Reveals Sophos today released findings of a dual…

The world is watching as Russia invade Ukraine with global leaders and public figures preaching a message of peace. However,…

Cybersecurity expert, 2016’s/2021’s Top 40 Under 40 winner, and featured in Tribe of Hackers, Dr Bright Gameli Mawudor, has revealed…

Recently, my Editor-in-Chief penned an article asking whether we ought to spell it as cyber-security, cybersecurity or cyber security. Through…
Medicine. Aeronautics. Academia. When you’re a cybersecurity professional, the colleague next to you could have started in one of these…

The following QnA included both Schneider Electric, and Fortinet representatives. 1. It is a year since the partnership between Schneider…
No more posts available. Thank you for scrolling this far.
No more posts available. Thank you for scrolling this far.