Midas Ransomware Attack Highlights the Risks of Limited Access Controls and “Ghost” Tools
There have been findings from an incident involving Midas ransomware that took place over two months and involved extensive lateral…

There have been findings from an incident involving Midas ransomware that took place over two months and involved extensive lateral…

According to Kaspersky’s latest research on the threat landscape trends, South Africa, Kenya and Nigeria are facing a dramatic change…

Cybersecurity is the process of securing networks, systems and any other digital infrastructure from malicious attacks. Malicious attacks vary, some…

It’s Cybersecurity Awareness Month at a time when cybersecurity awareness should be on everyone’s mind. The risk of attack has…

Recently, my Editor-in-Chief penned an article asking whether we ought to spell it as cyber-security, cybersecurity or cyber security. Through…
South Africa and the United Kingdom will today co-host the inaugural Information Communication Technology (ICT) Cyber Dialogue. According to the…
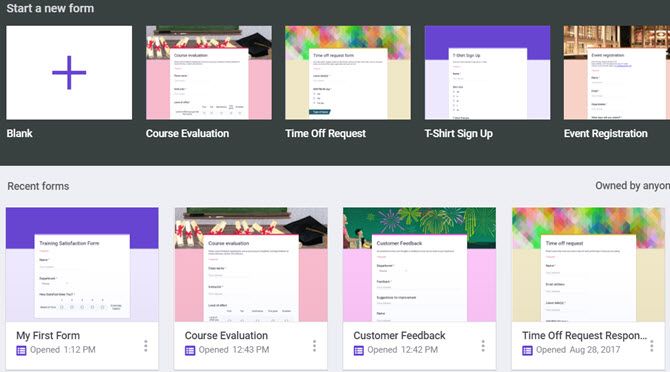
Sophos has published a research titled Phishing and Malware Actors Abuse Google Forms for Credentials, Data Exfiltration, that describes how…

Imagine if your mobile phone could be used to spy on you, listen to your conversations and send information and…

Check Point Research, the Threat Intelligence arm of Check Point® Software Technologies Ltd, a leading provider of cyber security solutions…

Our digital cosmos is continuously evolving from technology, process, and people standpoints. As corporations adapt to more innovative technologies and…
No more posts available. Thank you for scrolling this far.
No more posts available. Thank you for scrolling this far.