advertisement
How to protect your business from holiday attacks
It’s the holiday season, and that’s when we often make it easier for attackers to do their business. For example,…

It’s the holiday season, and that’s when we often make it easier for attackers to do their business. For example, consider the out-of-office replies that we attach to messages. This time of year, it’s typical for people to take time off between Christmas and the New Year. Those out-of-office messages often contain key information about how long the person will be out of the office, where they might be going, information about their office location, or their assistants and co-workers that attackers may and can use to perform social engineering attacks against the organization.
Your organization might want to limit out-of-office messages to just be sent internally. You can also use PowerShell to determine when people set up an out-of-office message inside the firm.
advertisement
Of course, out-of-office messages aren’t the only way attackers can get social information about your organization. The best attackers already know about you and your organization from LinkedIn, already know about holiday trips and plans from Instagram and Facebook, and won’t care if you are in the office because they plan to attack you quietly. They may, in fact, attack your organization during a busy time as the events in the logs will be buried with all the other normal traffic.
UEBA settings to spot unusual holiday behavior
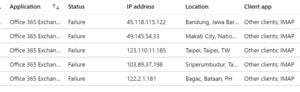
User and entity behavior analytics (UEBA) technology looks for multiple concurrent logins, impossible logins based on geography, unusual file access as well as password spray techniques. For users of Azure and Office 365, you should review the options in Cloud App Security to identify these UEBA activities that don’t make sense in your organization. If you are on-premises, you can look at LogonTracer.
Add cloud application security to Azure and Office 365 subscriptions by setting up specific alerts to identify impossible logins and allow you to set rules accordingly. If you have an Azure P1 license, you can review logins to Azure AD and see how often you receive failure logins from unusual locations. For example, on my Azure AD you can see various locations from around the world.
advertisement
 SUSAN BRADLEY
SUSAN BRADLEYCloud App Security is part of the E5 license but can be purchased for $3.50 per user and added for high-risk users that that you may wish to alert for unusual activity. For example, I recommend that you add it to cover any potential targeted users as well as any global administrators to ensure that no one logs in from unusual locations.
Fighting targeted, macro-delivered attacks
Attackers also use the holiday season as a cover for targeted attacks. Microsoft Security Intelligence pointed out that targeted Emotetattacks use enticing headlines such as “Holiday party” or other holiday themes that users typically see this time of year. Emotet uses a variety of attack methodologies to gain access to your systems. The infection may arrive either via malicious script, macro-enabled document files or malicious links.
Often these malicious documents include macros that are used to launch the attack. Microsoft sees Office documents as potential carriers of malicious macros and is in early testing of a tool to help block them, Office Application Guard. It will add sandbox features to Office applications and aims to isolate the document’s access to the rest of the machine and network. Even if a malicious macro or security bug is exploited, the bad code won’t be able to access other parts of the computer.
advertisement
How can you protect your system from malicious macros? Plenty of ways. Start by ensuring that you are up to date on Office patches. Every month Office receives several updates, many to fix remote code vulnerabilities.
Most firms that use Excel enable macros. You can set up Excel to be smarter about how it uses and trusts worksheet macros. The National Cyber Security Centre points out that macros are the majority of attacks in Office documents. They recommend the following settings in your Office programs:
- Disable Office macros except in the specific apps where they are required.
- Enable macros only for staff that rely on them.
- Use an anti-malware product that integrates with the Anti Malware Scan Interface (AMSI) on Windows 10 (or use the default of Windows Defender).
- Use the latest version of Office (ideally the Monthly Channel) on the latest version of the platform
Remember that in current versions of Office, the user must enable macros and they do not work by default. It issues a yellow warning banner when you open up a file that contains macros from the internet. Educate your users of these warnings and messages and ensure they understand when to enable and when to not enable these Office files.
 SUSAN BRADLEY
SUSAN BRADLEYAt a minimum, digitally code sign your internal macros to ensure that your users can trust them. With online alternatives such as Forms, Flow and PowerApps — as well as various web applications — it may be time to review whether it’s wise to use Office macros at all in your office.
Review your Office policies. If you worry about the risk of out-of-office messages, maybe it’s time to review how your firm uses Office documents. Look at the risks of macros and review what you can do in your office to ensure the new year is more secure.
Don’t forget to sign up for TechTalk from IDG the new YouTube channel for tech news of the day. You can also go back and review the videos for the year of 2019 as we start off 2020.