advertisement
Hacker allegedly stole logins from a US election agency
A Russian-speaking hacker has been found selling stolen login credentials for a U.S. agency that tests and certifies voting equipment,…
A Russian-speaking hacker has been found selling stolen login credentials for a U.S. agency that tests and certifies voting equipment, according to a security firm.
The hacker was attempting to sell more than 100 allegedly compromised login credentials belonging to the U.S. Election Assistance Commission (EAC), the security firm Record Future said in a Thursday blog post. The company said it discovered online chatter about the breach on Dec. 1.
Some of these credentials included the highest administrative privileges. With such access, an intruder could steal sensitive information from the commission, which the hacker claimed to have done, Recorded Future said.
advertisement
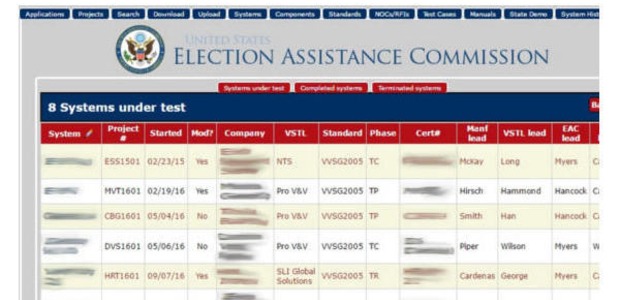
According to screenshots obtained by Recorded Future, the hacker had access to details about tests of election systems and software.
The EAC said it has terminated access to the affected application and is working with federal law enforcement to determine the source of the criminal activity.
The EAC was formed in 2002. In addition to certifying voting systems, it develops best practices for administering elections.
advertisement
In a statement, the commission said that it was aware of a “potential intrusion” involving a web-facing EAC application.
The possible breach comes after weeks of allegations that the Russian government attempted to influence last month’s U.S. election through several high-profile hacks.
The commission does not directly administer U.S. elections. They are carried out by states and local jurisdictions.
advertisement
“The EAC does not maintain voter databases. The EAC does not tabulate or store vote totals,” the commission said.
Record Future also said the hacker it identified doesn’t appear to be sponsored by any foreign government. The security firm’s blog post didn’t cite any evidence that the hack had resulted in vote-tampering in the election.
To pull off the breach, the hacker exploited an unpatched SQL injection vulnerability, a common attack point found in websites. The hacker may also have tried to sell details about this vulnerability to a broker working on behalf of a Middle Eastern government, Recorded Future said.
“It’s not uncommon for this type of vulnerability to lead to broader system level access, however, in this case the full extent of the EAC compromise remains unknown,” Recorded Future said.
The stolen login credentials could have also allowed a hacker to modify or plant malware on the commission’s web-facing application, the company said.
It’s unclear how long the vulnerability remained unpatched, so it’s possible other bad actors may have exploited it, Recorded Future said.