advertisement
#AfrSS2017: Kenya hit by WannaCry ransomware underlining the vulnerability of local firms
The attack wreaked havoc on organisations like Telefónica and several other large companies in Spain, as well as parts of…
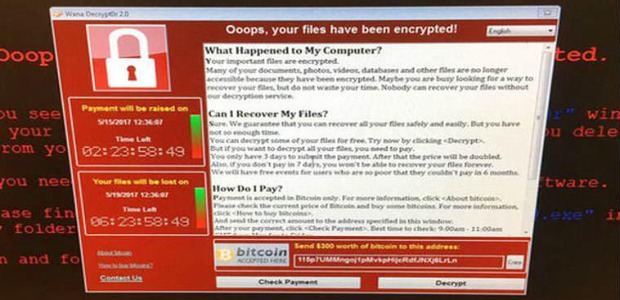
The attack wreaked havoc on organisations like Telefónica and several other large companies in Spain, as well as parts of Britain’s National Health Service (NHS) where operations were cancelled, X-rays, test results and patient records became unavailable and phones did not work, FedEx, Deutsche Bahn, and LATAM Airlines. Other targets in at least 99 countries were also reported to have been attacked around the same time.
Like previous ransomware, the attack spreads by phishing emails, but also uses the EternalBlue exploit developed by the U.S. National Security Agency (NSA) to spread through a network which has not installed recent security updates to directly infect any exposed systems. A “critical” patch had been issued by Microsoft on 14 March 2017 to remove the underlying vulnerability for supported systems, but many organizations had not yet applied it.
Those still running exposed older, unsupported operating systems were initially at particular risk, such as Windows XP and Windows Server 2003, but Microsoft has now taken the unusual step of releasing updates for these.
advertisement
Shortly after the attack began, a web security researcher known by his Twitter account MalwareTech, found an effective kill switch which slowed the spread of infection, but new versions have now been detected that lack the kill switch.
Fortunately for African organisations the attacks started late on Friday when most organisations/employees had left their offices for the weekend though The Communications Authority of Kenya (CA), through the National Kenya Computer Incident Response Team Coordination Centre (National KE-CIRT/CC), said in a statement that they has received confirmed reports of an encryption based cyberattack, in the form of ransomware, that is targeting computers running the Windows operating system and is spreading worldwide.
In fact according to Business Daily at least 5 companies in Kenya have been hit Wannacry, amid warnings by tech experts underlining the vulnerability of local firms and it is expected to get worse as about 80 per cent of the country’s large and small organisations’ back-up systems run on Microsoft Windows, which is the malware’s target.
advertisement
So what impact does the attack have? According to a statement by Serianu, once the initial worm module introduced to a system it creates two threads. The first thread scans hosts on the LAN. Whereas, the second thread gets created 128 times and scans hosts on the wider Internet.
The LAN-based scanning happened using the port 445 and attempts to exploit the discovered systems using MS17-010/ETERNALBLUE. On the other hand, the second thread scan the Internet by generating random IP addresses. If connection to port 445 on that random IP address succeeds, the entire /24 range is scanned, and if port 445 is found open, exploit attempts are made. Therefore, if the target network has the vulnerability unpatched, then there is a high chance that it will get affected.
According to Mr. William Makatiani, CEO of Serianu some recommended Steps for Prevention of similar attacks would include applying the Microsoft patch for the MS17-010 SMB vulnerability dated March 14, 2017.
advertisement
Organisations should as well enable strong spam filters to prevent phishing e-mails from reaching the end users and authenticate in-bound e-mail using technologies like Sender Policy Framework (SPF), Domain Message Authentication Reporting and Conformance (DMARC), and DomainKeys Identified Mail (DKIM) to prevent e-mail spoofing.
“Almost 80 per cent of our servers are based on Windows, we have another almost 16 per cent on unix or the Linux variant and then you have other operating systems … we are very vulnerable. To stay safe try to scan all incoming and outgoing e-mails to detect threats and filter executable files from reaching the end users and ensure anti-virus and anti-malware solutions are set to automatically conduct regular scans,” added Mr. Makatiani.
Another safety measure would be managing the use of privileged accounts. Implement the principle of least privilege. No users should be assigned administrative access unless absolutely needed. Those with a need for administrator accounts should only use them when necessary.
Windows users have also been urged to configure access controls including file, directory, and network share permissions with least privilege in mind. If a user only needs to read specific files, they should not have write access to those files, directories, or shares. There is also need to disable macro scripts from Microsoft Office files transmitted via e-mail. Consider using Office Viewer software to open Microsoft Office files transmitted via e-mail instead of full Office suite applications.
According to the latest cybersecurity report by Serianu Kenya alone was estimated to have lost about Sh18 billion to hackers who siphoned from or blackmailed businesses and individuals.