advertisement
Perspective – Aftermath of the WannaCry Attack
The WannaCry exploit was global news, but it seems to have died down. Is the worst over, or is this…
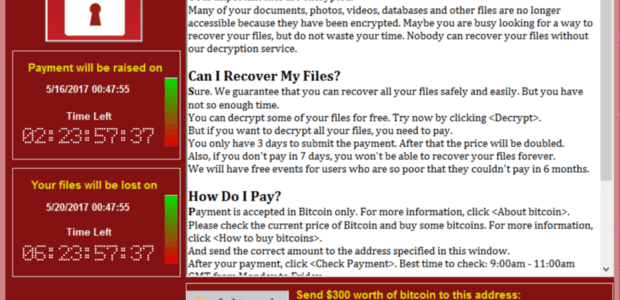
The WannaCry exploit was global news, but it seems to have died down. Is the worst over, or is this just the eye of the storm?
For a number of reasons, I believe that the WannaCry crisis has subsided. All exploit kits have a half-life. I believe that this vulnerability (SMB CVE 2017-0144) is past its high water mark in large part because cyber criminals have lost the element of surprise. This is also thanks to the global cooperation of members of law enforcement, national CERT, and the Cyber Threat Alliance.
There are rumors that a wave of new attacks, like Adylkuzz, are lining up to follow the WannaCry attack.
advertisement
A botnet that operates on stealth is always going to enjoy much more success, and may be more difficult to detect, than one we are prepared for. Once a large-scale, surprise attack occurs, everyone begins bracing for the next attack. Most organizations have already closed those doors and are now on high alert looking for a repeat of the WannaCry or a similar exploit.
Global telecommunication providers have also begun to block port 445 as well to further reduce the spread of the SMB exploit, which will hinder Adylkuzz even more. For these and similar reasons, copycat attacks, IMO, are severely impaired right now.
In addition, we are currently not seeing any indication that another attack like Adylkuzz is going to be able to ride this particular exploit to fuel a large outbreak. That’s not to say, however, that the malware creators could not find another tactic to make Adylkuzz a success.
advertisement
What indications are you referring to?
With millions of security sensors in place around the world, the FortiGuard Labs threat research team keeps its finger on the pulse of the global threat landscape. For example, FortiGuard data showed a number of exploits and probes leading up to the explosion of growth when adversaries caught organizations with their guard down. (There was a 340% uptick in activity against CVE-2017-0144, the SMB vulnerability DoublePulsar used to spread WannaCry.) Since then, we have seen a very large and steady decline in attack activity.
Since the attack’s high watermark on Friday and Saturday, we observed a -44% growth rate by Sunday. Since then, exploit activity has halved every day. Global attack numbers are now down 53% since the high water mark, from six figures of daily attacks to five, and we expect that trend to continue. This is generally because most vulnerable systems have now already been affected or hardened.
advertisement
As a result, the WannaCry (and AdyllKuzz) attack surface has significantly shrunk. Which means that similar attacks are showing up late to the race. Because they have lost the element of surprise, and detection and countermeasures are in place, slow and steady will not win this race.
So, was WannaCry the wildly successful exploit that many news agencies are reporting it was?
It depends on how you measure success. WannaCry has proven that non-zero day attacks can be wildly successful. However, it was a failure in terms of a ransom campaign (analysis of the attacker’s Bitcoin wallets indicates that not a lot of money paid out.) While WannaCry was impactful and quick, it was also by no means the largest botnet we have seen.
In terms of ransomware bots, the Cyber Threat Allianceobserved over 400,000 attempted ransom infections by CryptoWall v3 in 2015, which is nearly twice as large as what has been alleged for WannaCry. And with regards to silent Trojans/botnets, we have observed an infection base (the Mariposa botnet) with over 15M victims.
Large botnets such as these have a much larger attack surface because they are actively fueled by CaaS (crime as a service), with black hat affiliates who distribute them using their own attack methods.
So, if the WannaCry attack is largely over, what’s next on the threat horizon?
With so much global focus on the ShadowBroker exploit kit, Black Hat cybercriminals will likely hunt elsewhere on the DarkNet to find other potentially effective, fresh exploits that are not in the spotlight. Their goal will be to regain the element of surprise. Keeping in line with our2017 predictions, I believe we will likely see the world’s largest botnet, surpassing the high water mark of 15M+ infections.
We will most likely see that occur through the exploitation of IoT, resulting in the ransoming of IoT devices, services, critical data, and other intellectual property. Criminal activity such as collecting data, targeted attacks, and obfuscating other threats are likely to follow.
(The author is a Global Security Strategist, Fortinet).