advertisement
How to stop wasting money on security shelfware
A 2015 survey by Osterman Research, sponsored by Trustwave, illustrated just how bad the problem is. In a report of…
A 2015 survey by Osterman Research, sponsored by Trustwave, illustrated just how bad the problem is. In a report of 172 small-, medium- and large-sized enterprises, researchers found that those investing in new security controls often ended up underutilizing the technologies in which they just invested — or simply not using them at all.
Osterman found this to be true with at least 30 percent of the respondents. In some companies, survey respondents said nearly 30 percent of all new security investments were not being used at all or were underutilized. One company surveyed said 60 percent of its security software was shelfware.
“We expected some security software on the shelf,” said Josh Shaul, Trustwave’s vice president of product management at the time. “What we found was companies are pouring money down the drain.”
advertisement
How common is shelfware?
Shelfware is a common concern for many businesses, and it is often the result of little to no vendor consultation, too much emphasis on compliance before security and an unawareness of what the technology can truly do.
Indeed, a previous 451 Research report suggested that shelfware often resulted from over-hyped products, or solutions lacking features, and pointed to security information and event management (SIEM) and intrusion detection system (IDS) solutions as the most underused technologies. Many believe SIEM has long failed to live up to its marketing hype, while Target supposedly spent over $1 million on an anti-malware solution poorly configured at the time of its 2013 data breach.
advertisement
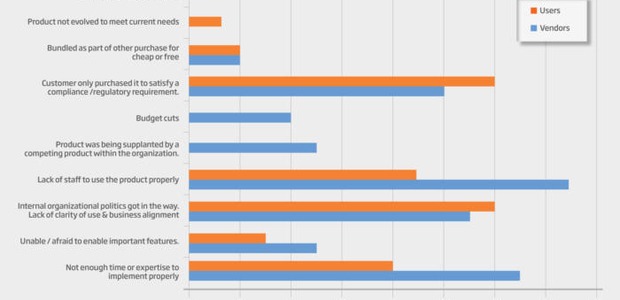
Users and vendors have different views of why products are not used or undertutilized.
This brings the question as to how such hi-tech solutions end up gathering dust. “The top three reasons from a customer perspective that security software ends up on the shelf is they only purchased it to satisfy a compliance or regulatory demand; internal organizational politics got in the way (or a lack of clarity of use and business alignment), and not enough time or expertise to implement properly,” says Javvad Malik, security advocate at Alienvault.
He argues it’s hard to change as far as compliance is concerned but says for the other two reasons, “It illustrates tactical purchasing or inheriting security technologies that have no place in the overall security strategy. There’s some shelfware that I’ve seen that literally has never been deployed and only purchased to satisfy an auditor.”
advertisement
“Those actually are probably the easiest to manage in that they are only a cost to the organization. The tougher ones are where the product is installed across the estate and then not maintained. It’s a bit like when people go to redecorate their home, and instead of stripping the wallpaper, skimming the wall and starting again, they just put new wallpaper up on the old one and add a coat of paint,” adds Malik.
Thom Langford, CISO at communications company Publicis Group, believes shelfware is often the result of security structure and that age-old concern over reporting lines. “I think the problem very much depends on how the security team is established and governed,” he says. “For instance, if a security team is a part of the IT team, I would suggest that this would exacerbate a shelfware problem as the security problem is looked at through a technology lens potentially leading to needless product purchase. If it sits outside of the IT remit, a more holistic approach can be taken allowing IT to purchase where it makes sense but only where it makes sense.”
Is the problem getting worse?
Malik suggests the problem is getting worse, something Langford agrees with, pointing to the “huge amount of hype and swagger” from vendors often selling products through fear, uncertainty and doubt. “With security budgets increasing, a lot of silver bullets are being invested in blindly before fundamental are in place in their organizations,” Langford adds.
Malik, though, believes the rise of software as a service (SaaS) has some saving grace: “With more services being cloud-based and security increasingly heading to the cloud, the problem is getting less severe as cloud services can be typically easier to deploy and rollback. Also, it’s easier to run a trial, or month to month subscription. It removes the capital expenditure needed for large on premises deployments.”
Phil Cracknell, interim CISO at home repairs company HomeServe, agrees: “Software as a service or a flexible annual licence tariff can help. Insist on a model whereby you pay for what you use. Reject the price breakpoints because they benefit the vendor, not you.”
Fixing the vendor problem
The shelfware problem for many CISOs is not helped by security vendors and their commission-hungry sales teams. Indeed, it’s not unusual for infosec pros to complain of vendors doing too much selling and too little educating CISOs in building their security stack.
Cracknell is one of those, saying that today’s vendors sell comprehensive solutions with anti-virus, data leak protection (DLP), host-based intrusion detection system (HIDS) and network access control (NAC) all built in — even if the customer doesn’t understand the suite’s full capabilities. He believes vendors are now controlling the market. “[The danger is] we let the vendors control the market as they did a few years back. They are starting to again. They define what products and technologies exist and then embark on a campaign to convince us that we need it. We should be defining the requirements we have, risks we see and need addressing and the vendors produce solutions in a way that can be consumed effectively by us. The tail needs to stop wagging the dog.”
Langford, to a point, agrees adding that there must be a more open relationship between both parties. “Up-front consultancy and honesty is key; a vendor who tells me that their solution won’t work until I have fixed my own internal issues is going to get my money and more importantly my trust in the long term over one that is simply pushing me to sign on the dotted line. Always build a relationship with a vendor first. Get to know them and allow them to get to know you. See what else they are doing with other clients, and speak to them. How are they selling to you? Are they simply pushing to make the numbers or do they actually want to partner with you over the long haul and help you fix your problems?”
Malik says it ultimately comes to full-featured, fully functioning products that integrate with legacy equipment quickly and easily. “The final aspect is communication, finding out what the customer likes about the product, what can be improved, and taking that feedback on board.”
CISOs must sweat the assets
Shelfware is not inevitable, and it can be reduced or even eliminated by some proactive and surprisingly simple first steps.
Infosec professionals believe it comes down to a more controlled acquisition process, sweating the products you already have — and getting the basics right before acquiring new solutions. “First, leverage the products that have the broadest of capabilities, something that can give breadth of coverage,” says Malik. “This will help get a lay of the land and understand the challenging areas which can then be focussed on more specifically. Don’t try to boil the ocean, but start from critical assets. Finally, the best way is to experiment with the product and network with peers to see how they have deployed capabilities. Security doesn’t need to be a complex offering — often it boils down to doing the basics well and consistently.”
Langford says: “Focus on process, and people first. These two things can get you a long way towards your goals, sometimes far enough to not require further investment. Only when you understand your prices, how your organisation and people operate, and where you need technology support should that investment be made.”
Malik, finally, adds that CISOs and other IT decision makers should be questioning why a purchase is made, obtain stakeholder support early and develop a 30/60/90 plan, as well as have a deployment plan “fully fleshed out prior to purchasing.” He stresses, too, the importance of decommissioning old technology, verifying product capabilities and research.