advertisement
DownToEarth Technologies Slates Date for Zero Trust Approach Webinar
Digital Transformation has been fast tracked by the onset of the pandemic and it is now up to us to keep up with the changes. Most sectors are already digitizing and it is up to the players to keep up with the fast tracked digitization and digital transformation.
Cyber security, for instance, is one thing that most people are learning on the go. What most people used to know about Cyber security is apparently not enough as even the cyber attackers have devised new ways.
In this light, DownToEarth Technologies is organising a cyber security webinar that focuses on a Zero Trust approach to security. This is the approach that most cyber security professionals advise companies to use to protect their data and their clients’ data. The webinar has been slated for 28th April 2022.
advertisement
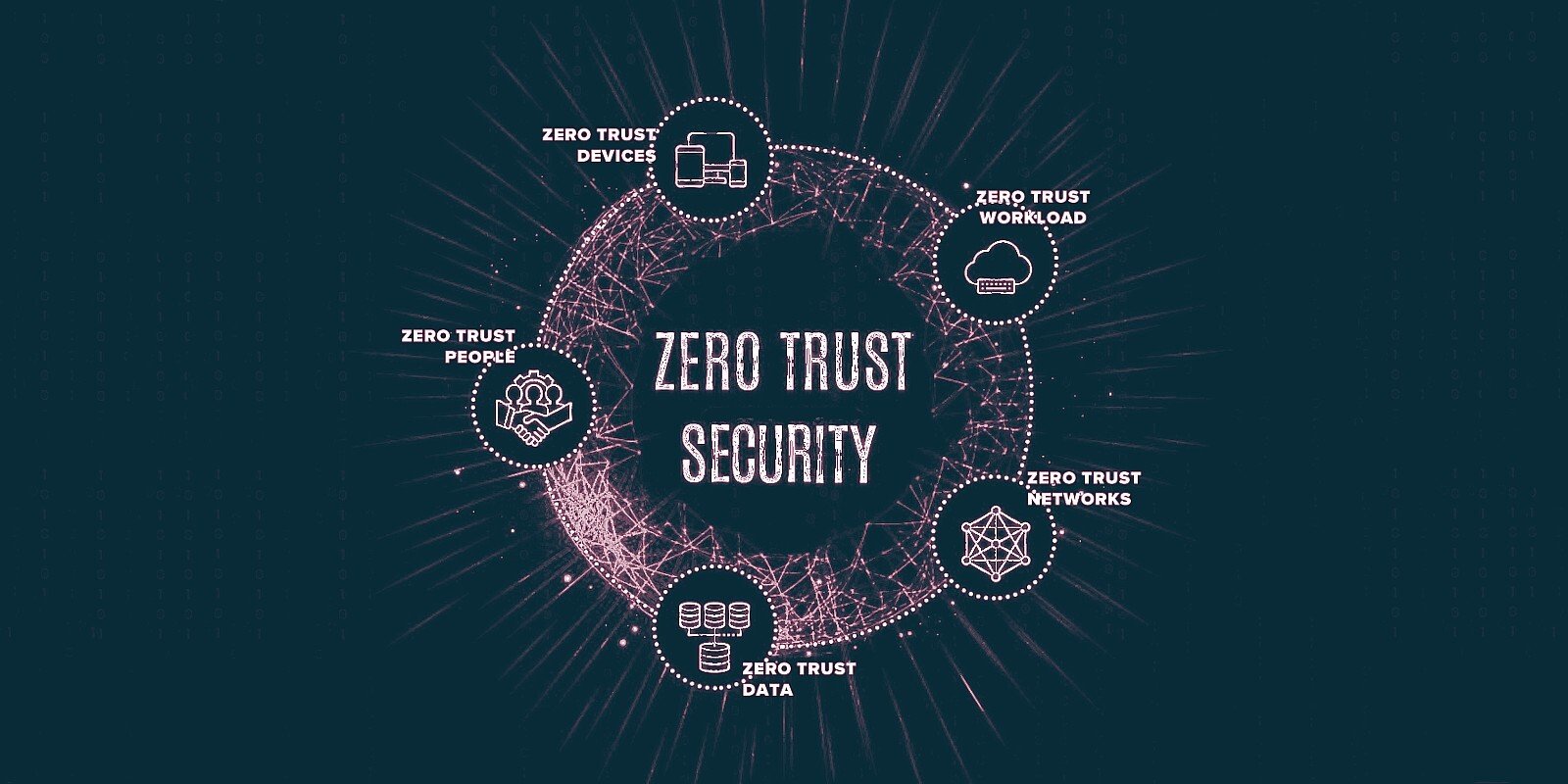
Traditional security approaches assume that anything inside the corporate network can be trusted. However, this assumption no longer holds true because of mobility, BYOD (Bring Your Own Device), IoT (Internet of Things), cloud adoption, increased collaboration, and a focus on business resiliency.
A zero-trust model is more preferred today because it considers all resources to be external and continuously verifies trust before granting only the required access.
Kelvin Mugambi, the Technical Solutions of Architect Security at CISCO and a championer of the Zero Trust approach model, will be giving the keynote talk at the webinar. DownToEarth Technologies’ Managing Director Vincent Milewa and the company’s Technical Manager Florence Munene will also be speaking at the webinar slated for 28th April.
advertisement
Zero trust is a strategic approach to security that centers on the concept of eliminating trust from an organization’s network architecture. Trust is neither binary nor permanent. We can no longer assume that internal entities are trustworthy, that they can be directly managed to reduce security risk, or that checking them one time is enough. The zero-trust model of security prompts you to question your assumptions of trust at every access attempt.
To join the webinar, register via link.