130 electronic fraud suspects hunted by police
The Directorate of Criminal Investigations (DCI) on Wednesday the 30th January 2019, published names and images of 130 suspects implicated…
Analytical stories of tech trends, products, services, moves and technologies including cloud computing, security, big data, analytics, internet of things, artificial intelligence, storage, blockchain

The Directorate of Criminal Investigations (DCI) on Wednesday the 30th January 2019, published names and images of 130 suspects implicated…

If you have any doubts that digital transformation is top of mind for IT executives, just take a look at what they’re…

A supply chain attack, also called a value-chain or third-party attack, occurs when someone infiltrates your system through an outside…
Cisco is rolling out a cloud-based geolocation package it expects will help customers grow mobile location services and integrate data…

The C-suite and boards of directors often think about investment decisions under three key pillars – Will this decision make…

Cloud computing has become the de facto platform for fueling digital transformations and modernizing IT portfolios. Companies are increasingly finding…

To take advantage of innovations like artificial intelligence you must first move away from manual processes. For that reason alone,…

When the late Apple CEO Steve Jobs introduced the iPhone 12 years ago, he also introduced to many the concept…
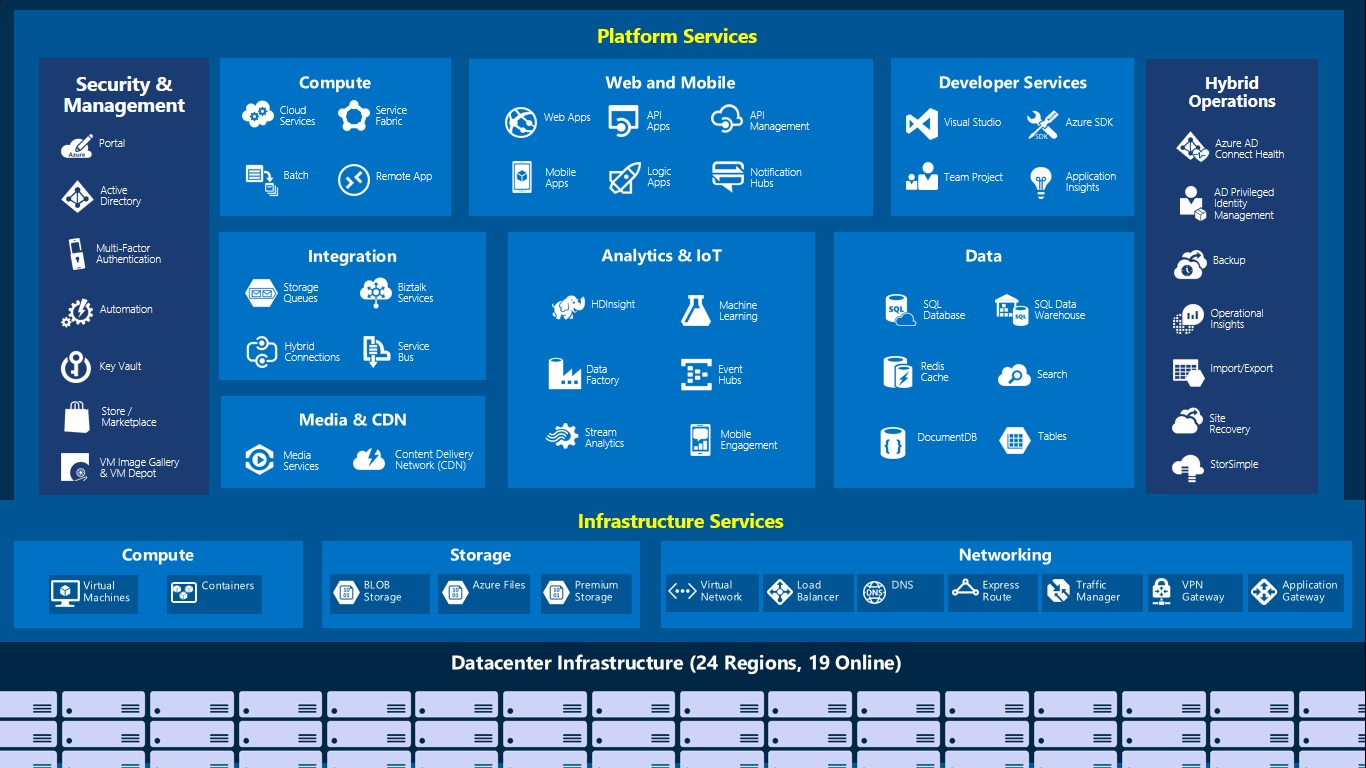
If you’re a Nairobi listed business you’re either a monolith or a dinosaur. There are two definitions of monolith in…

The Public Accounts Committee (PAC), in a report tabled on 3rd May 2018, asserted that JamboPay- the system contracted to…
No more posts available. Thank you for scrolling this far.
No more posts available. Thank you for scrolling this far.