advertisement
BeagleBoyz Resurgence Witnessed On American Soil

Since February 2020, North Korea’s BeagleBoyz have resumed attacking banks in several countries to initiate fraudulent international money transfers and ATM cashouts. Their recent resurgence follows a lull in bank targeting since late 2019.
To differentiate methods from other North Korean malicious cyber activity, the US government refers to this team as BeagleBoyz; representing a subset of Hidden Cobra activity. North Korea’s intelligence apparatus controls a hacking team dedicated to robbing banks through remote internet access. From as early as 2009, Hidden Cobra actors have expounded their capabilities to target and compromise a range of victims; some intrusions have resulted in the exfiltration of data while others have been disruptive.
Commercial reporting has referred to this activity as Lazarus Group and Guardians of Peace. DHS and the FBI assess that Hidden Cobra actors will continue to use cyber operations to advance their government’s military and strategic objectives.
advertisement
Tools and capabilities used by Hidden Cobra actors include DDoS botnets, keyloggers, remote access tools (RATs), and wiper malware.
The hack commonly targets systems running older, unsupported versions of Microsoft operating systems. The multiple vulnerabilities in these older systems provide targets for exploitation. Adobe Flash player vulnerabilities have also been used to gain entry into compromised networks.
A subset of the Hidden Cobra branch, the BeagleBoyz overlap to varying degrees with groups tracked by the cybersecurity industry. Advanced Persistent Threat 38 (APT38), Bluenoroff, and Stardust Chollima and are responsible for the FASTCash ATM cashouts reported in October 2018, fraudulent abuse of compromised bank-operated SWIFT system endpoints since at least 2015, and lucrative cryptocurrency thefts.
advertisement
This illicit behaviour has been identified by the United Nations (UN) DPRK Panel of Experts as evasion of UN Security Council resolutions, as it generates substantial revenue for North Korea. North Korea can use these funds for its UN-prohibited nuclear weapons and ballistic missile programs; this activity poses a significant operational risk to the financial services sector and erodes the integrity of the financial system.
This illicit behaviour has been identified by the United Nations (UN) DPRK Panel of Experts as evasion of UN Security Council resolutions, as it generates substantial revenue for North Korea.
The group is responsible for the sophisticated cyber-enabled ATM cash-out campaigns identified publicly as “FASTCash.” Since 2016, the BeagleBoyz have perpetrated the FASTCash scheme, targeting banks’ retail payment system infrastructure (i.e., switch application servers processing International Standards Organization [ISO] 8583 messages, which is the standard for financial transaction messaging).
Since the publication of the FASTCash report in October 2018, there have been two particularly significant developments in the campaign: (1) the capability to conduct the FASTCash scheme against banks hosting their switch applications on Windows servers, and (2) an expansion of the FASTCash campaign to target interbank payment processors.
advertisement
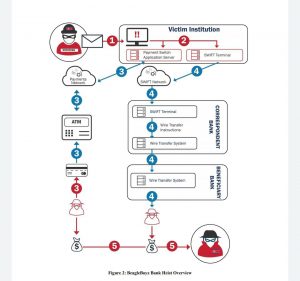
According to estimates, the BeagleBoyz were responsible for attempting to steal nearly $2 billion from various financial institutions in a coordinated cash-out attack in over 30 countries worldwide. The US government now attributes the BeagleBoyz as being behind the $81 million heist from a financial institution in Bangladesh. In contrast, past reports had linked it to Hidden Cobra/Lazarus activity. In addition, the BeagleBoyz have been linked to attacks in Africa and Chile since 2018.
The BeagleBoyz are now attributed by the United States government as being behind the $81 million heist from a financial institution in Bangladesh, whereas past reports had linked it to Hidden Cobra/Lazarus activity.
The primary modus operandi of the BeagleBoyz revolves around a history of social engineering, spear-phishing, and watering hole tactics. Contained within the Malware Analysis Reports (MAR) cited above are (13) unique malware samples. These are a combination of remote access tools/trojans (RAT), a tunnelling proxy tool, keylogger/screen capturing, and man in the middle attacks—all specifically targeting ISO 8583 Point of Sale (POS) system messages, ATM transaction requests, and ATM balance inquiries.
Along with the US, BeagleBoyz have stirred from their short lull and have been targeting banks in countries like Argentina, Chile, India, Japan, Mexico, South Korea, Spain and many others, according to the warning. China and Russia are notable exceptions to this point. BeagleBoyz also target cryptocurrency exchanges to steal large amounts of cryptocurrency, sometimes valued at hundreds of millions of dollars per incident, the alert said.