CA-Bureau of Statistics survey: Most Kenyan companies lack IT security policies
The Communications Authority and the Kenya National Bureau of Statistics have released their first-ever survey about ICT use and policies…
Analytical stories of tech trends, products, services, moves and technologies including cloud computing, security, big data, analytics, internet of things, artificial intelligence, storage, blockchain

The Communications Authority and the Kenya National Bureau of Statistics have released their first-ever survey about ICT use and policies…

The average price of data visualization software has dipped at a 0.8% annual rate in the past three years, primarily…

DefendDefenders is calling for applications to its Safe Sister Fellowship for women from East Africa; the program is dubbed, ‘Safe…

The countdown to the United Kingdom’s separation from the European Union began in late March when U.K. prime minister Theresa…

To enable such automation, precisely timed system control must be possible. One prime example of the need for such precise…

However, IoT has had limitations especially relating to standardization. This has seen the emergence of new technologies like The Low…
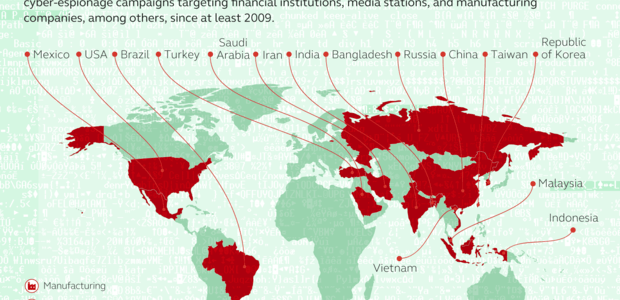
Kaspersky Lab has published the results of its more-than-year-long investigation into the activity of Lazarus – a notorious hacking group…
Transporting freight operates at a massive scale in the U.S., most of it hauled by trucks that are the lifeblood…

Attackers prefer to reuse code and tools for as long as they keep working. In that tradition, researchers have found…

Internet penetration in Kenya grew by 4.4 percent between October and December 2016 to reach 89.7 per cent up from…
No more posts available. Thank you for scrolling this far.
No more posts available. Thank you for scrolling this far.